Do You Need an OT Security Operations Center?
Integrating Operational Technology into a Security Operations Center: DeepSeas Navigates the Unique Challenges
Our crew at DeepSeas is often asked our perspective on Operational Technology (OT) – specifically how organizations can extend their cybersecurity program into the OT space and whether or not an organization needs a Security Operations Center (SOC) dedicated solely to OT. Is the OT challenge unique and different enough from traditional IT to justify a dedicated team of security specialists focused Operational Technology?
Our thoughts on the topic can be illustrated best with this Venn diagram, which represents the similar and differing challenges of OT and IT. You’ll see there is a large overlap between the two in detection and analytics. Underscoring that detections and the analysis of those detections is similar enough across these environments that, with the proper specialized training, a security specialist can successfully analyze both OT and IT alerts.
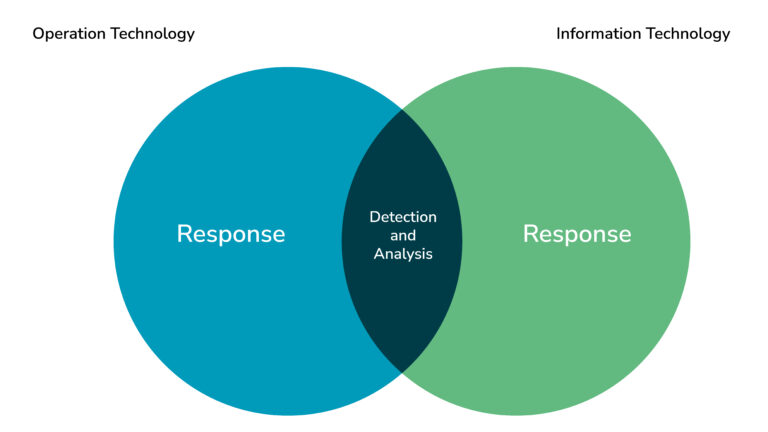
However, the response in OT and the response in IT are fundamentally separate and distinct. In Operational Technology environments, you could potentially have a system that is working to produce a $100 million batch of medication or is in the middle of doing CNC work on a jet engine, and you simply cannot interrupt that process without incurring a substantial business risk or loss. This is where mitigation versus remediation come into play. Often in OT, once a threat has been detected, efforts must initially focus on mitigation of that threat so that whatever batch process can work to completion. Focus can then shift to a full remediation of the threat.
Key Enablers
People
An escalation point is imperative, as the response process must involve the client organization. Clients must identify someone within their organization who is onsite, has access to the necessary systems, and the right professional for a member of the DeepSeas SOC crew can contact in the case of an event. This person must be available and able to support the response needed to mitigate and/or remediate a particular threat. This need is often new to manufacturing organizations and can result in the need for cross-organizational transformation. This blends directly into the next key enabler – process.
Process
The person within the client organization who is responsible for working an active threat with the DeepSeas SOC crew must understand the batch processes that are happening on the shop floor and what the proper response actions need to look like at the time of an incident.
There are also adjustments that DeepSeas will make to ensure effective response when responding to an OT threat. Our SOC analysts understand that interfacing with an Operational Technology environment is fundamentally different from a standard IT environment. Consequently, playbooks and runbooks are updated to account for this fact.
Technology
Critical to securing OT environments is the implementation of OT-centric detection and response technologies – whether it’s agent-based endpoints or more passive listening to the lower levels of the Purdue model that you have on your manufacturing floor – critical visibility into these layers is absolutely essential to the success of any detection and response efforts.
At DeepSeas, we advocate for a transformative understanding of the Operational Technology landscape, recognizing its unique challenges and distinctions from traditional IT environments and safeguarding its critical processes.
