


DeepSeas Goes
Deeper
An all-in-one cybersecurity solution that finds<br> every hole in your defense, and then fixes it for you.
These Great Organizations Trust DeepSeas










Every Risk Has a Response
Pick one solution or let us tailor the right protection package for you.
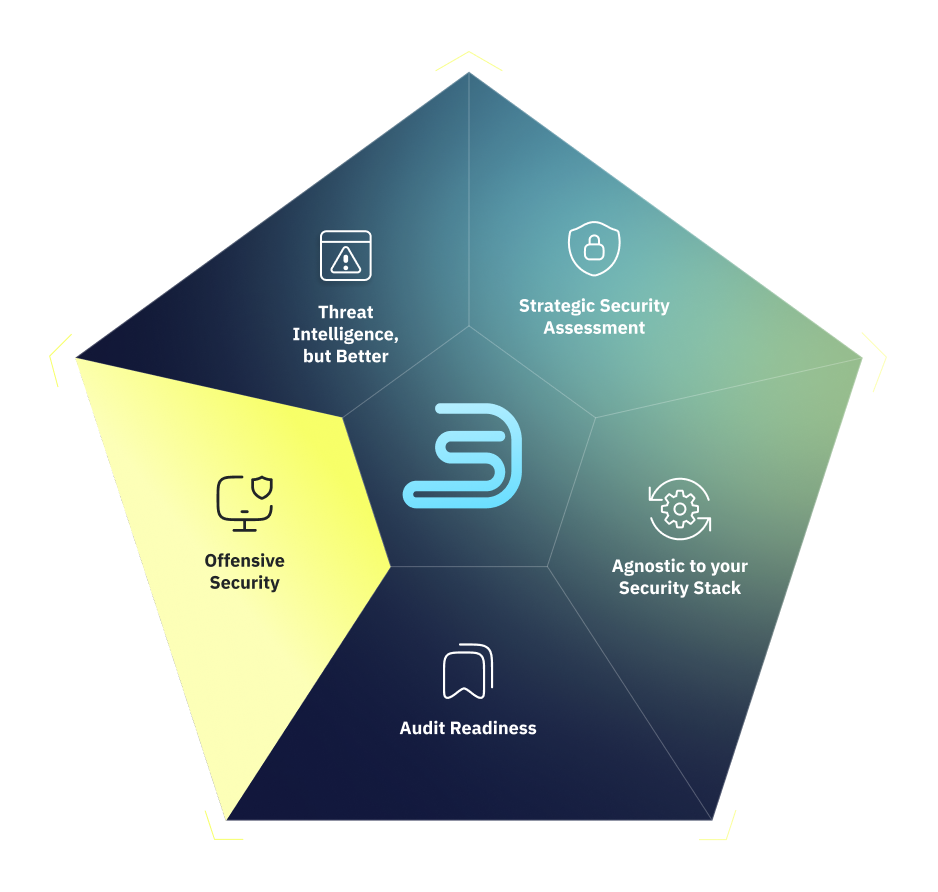
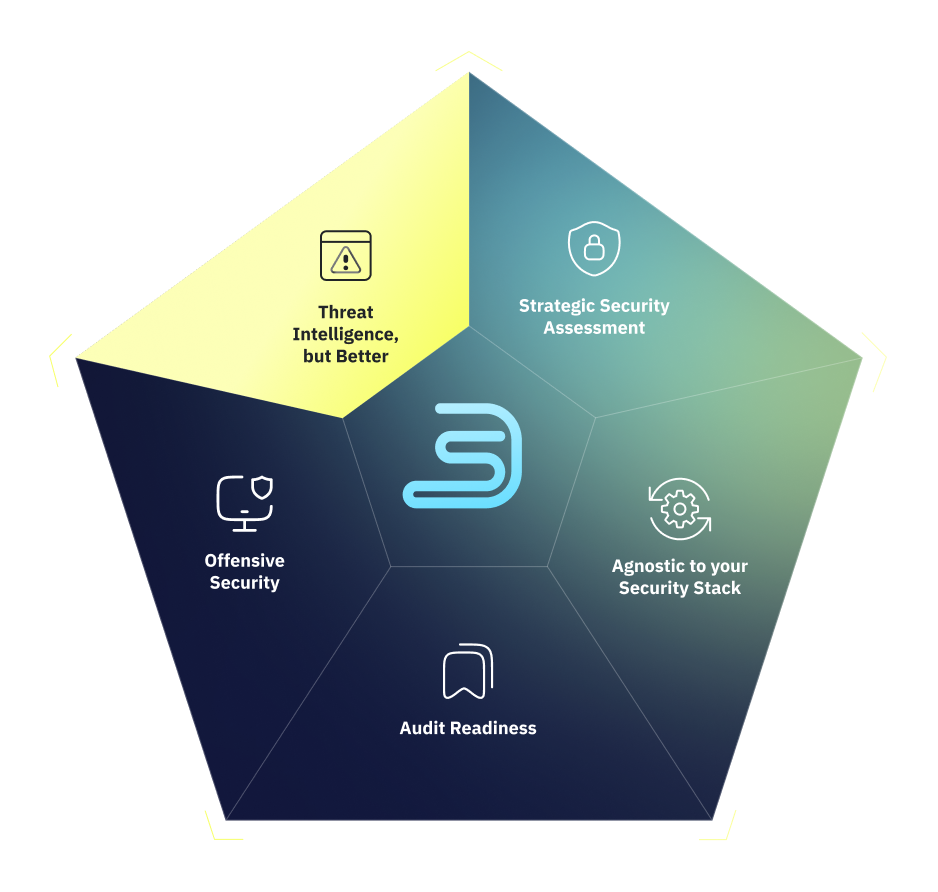



Complete Defense Starts With Depth
Most security threats aren’t surface-level – they’re rooted deeper. Surface-level solutions are simply not enough to fix them.
We built DeepSeas Complete on that principle, tapping battle-tested security experts to engineer an offering that goes as deep as needed, on everything that matters (and discards everything that doesn’t).



An AI Platform That Sees Deeper
The DeepSeas Platform integrates all major security alert and response systems into one source of truth, enriching them with deep context in the process.
By doing so, DeepSeas uncovers threats that siloed tools miss—correlating signals across your entire stack to provide defense that reaches root causes, not just surface symptoms.














