threat-analysis
OneNote Files Used for Malware Delivery, Actors Iterate Rapidly
February 3, 2023
OneNote Files Used for Malware Delivery, Actors Iterate Rapidly
A DeepSeas Summary
DeepSeas has identified a new technique involving the use of OneNote files in malware delivery, though activity of this nature was observed to have accelerated among cybercriminal groups in December 2022. The use of this new filetype has kicked off a rapid series of iterations from various threat actors to deliver their malware, especially among actors specializing in delivering commodity malware. These actors then commonly sell their access to other groups for monetization or further compromise (i.e., ransomware).
The malicious OneNote files contain embedded portable executables (.EXE), batch files (.BAT), link files (.LNK), HTML Application files (.HTA), as well as HTML containing JavaScript. In this last case, the authors of the QakBot malware most recently began using OneNote files to drop and execute their signature malware. In addition to QakBot, campaigns using malicious OneNote files have been identified delivering AsyncRAT, the RedLine infostealer, NetWire RAT, Quasar RAT, and the AgentTesla keylogger.
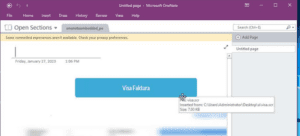
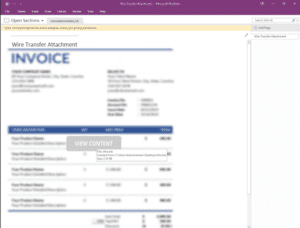
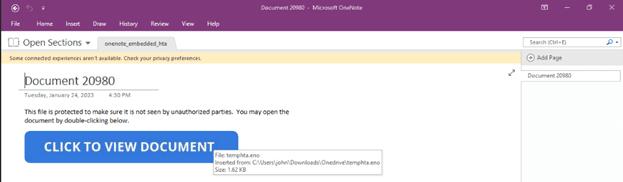
Adoption of this tactic among cybercriminals is hardly surprising, though the speed at which these groups have adopted it is notable. Throughout 2022 the malware delivery landscape was dominated by malicious LNK files (and sometimes disk image files containing malicious LNK files). While these are still observed, a notable portion of new malware delivery attempts are utilizing OneNote files. Corporate environments often make use of the full Microsoft Office suite of products rather than limited personal editions, thus they are at particular risk from this technique. In addition to heightened success rates against a variety of small, medium, and large businesses, DeepSeas expects these techniques to grow in complexity as these early attempts are countered.
Addendum
DeepSeas has developed Yara signatures to detect various malicious techniques related to use of the OneNote file format, which are provided below. These rules should be tested before deploying in a production environment:
rule Production_Detection_OneNote_EmbeddedFile_PE
{
meta:
author = "DeepSeas"
description = "OneNote with Embedded PE"
hash = "976a04848f2318829c9b732b9204a204f32985e09984ec655d6a9ecaf14db82e"
reference = https://www.securityondemand.com/onenote-files-used-for-malware-delivery-actors-iterate-rapidly/
strings:
$embedded_magic = "\xe7\x16\xe3\xbd\x65\x26\x11\x45\xa4\xc4\x8d\x4d\x0b\x7a\x9e\xac"
$onenote_hdr = "\xe4\x52\x5c\x7b\x8c\xd8\xa7\x4d\xae\xb1\x53\x78\xd0\x29\x96\xd3"
condition:
$onenote_hdr at 0 and
for any i in (0..#embedded_magic) : (
uint16(@embedded_magic[i] + 36) == 0x5a4d
)
}
rule Production_Detection_OneNote_EmbeddedFile_Lnk
{
meta:
author = "DeepSeas"
description = "OneNote with Embedded lnk"
hash = " f3aa175a1d0e8300f923b9a73bf250af99ce67b03a09558b449ea3b09dd59750"
reference = https://www.securityondemand.com/onenote-files-used-for-malware-delivery-actors-iterate-rapidly/
strings:
$embedded_magic = "\xe7\x16\xe3\xbd\x65\x26\x11\x45\xa4\xc4\x8d\x4d\x0b\x7a\x9e\xac"
$onenote_hdr = "\xe4\x52\x5c\x7b\x8c\xd8\xa7\x4d\xae\xb1\x53\x78\xd0\x29\x96\xd3"
$lnk_clsid = { 01 14 02 00 00 00 00 00 C0 00 00 00 00 00 00 46 }
condition:
$onenote_hdr at 0 and
for any i in (0..#embedded_magic) : (
$lnk_clsid in (@embedded_magic[i]+36..@embedded_magic[i]+36+uint32(@embedded_magic[i]+16))
)
}
rule Production_Detection_OneNote_EmbeddedFile_HTML
{
meta:
author = "DeepSeas"
description = "OneNote with Embedded html"
hash = " 5c0494ffa459829c4d553218a71d1b97f7cb0e4760cb27ff78745a3fdf2b2b18"
reference = https://www.securityondemand.com/onenote-files-used-for-malware-delivery-actors-iterate-rapidly/
strings:
$embedded_magic = "\xe7\x16\xe3\xbd\x65\x26\x11\x45\xa4\xc4\x8d\x4d\x0b\x7a\x9e\xac"
$onenote_hdr = "\xe4\x52\x5c\x7b\x8c\xd8\xa7\x4d\xae\xb1\x53\x78\xd0\x29\x96\xd3"
$html_contents01 = "<html" nocase
$html_contents02 = "<script" nocase
$wsh_shell = "WScript.Shell" nocase
condition:
$onenote_hdr at 0 and
for any i in (0..#embedded_magic) : (
($html_contents01 in (@embedded_magic[i]+36..@embedded_magic[i]+36+uint32(@embedded_magic[i]+16)) and
$html_contents02 in (@embedded_magic[i]+36..@embedded_magic[i]+36+uint32(@embedded_magic[i]+16)) ) or
$wsh_shell in (@embedded_magic[i]+36..@embedded_magic[i]+36+uint32(@embedded_magic[i]+16))
)
}
rule Production_Detection_OneNote_EmbeddedFile_HTA
{
meta:
author = "DeepSeas"
description = "OneNote with Embedded HTA"
hash = " 017b1967ece61631b8f04108ee92c22881803d4c21281ef88fad5900e09f466b"
reference = https://www.securityondemand.com/onenote-files-used-for-malware-delivery-actors-iterate-rapidly/
strings:
$embedded_magic = "\xe7\x16\xe3\xbd\x65\x26\x11\x45\xa4\xc4\x8d\x4d\x0b\x7a\x9e\xac"
$onenote_hdr = "\xe4\x52\x5c\x7b\x8c\xd8\xa7\x4d\xae\xb1\x53\x78\xd0\x29\x96\xd3"
$hta = "HTA:APPLICATION" nocase
condition:
$onenote_hdr at 0 and
for any i in (0..#embedded_magic) : (
$hta in (@embedded_magic[i]+36..@embedded_magic[i]+36+uint32(@embedded_magic[i]+16))
)
}
rule Production_Detection_OneNote_EmbeddedFile_BAT_VBS
{
meta:
author = "DeepSeas"
description = "OneNote with Embedded BAT or VBS"
hash = "b9241b7be9b0ff3f8d1686657f5722ec778797471b3b81d364af6ef952c0a39d"
reference = https://www.securityondemand.com/onenote-files-used-for-malware-delivery-actors-iterate-rapidly/
strings:
$embedded_magic = "\xe7\x16\xe3\xbd\x65\x26\x11\x45\xa4\xc4\x8d\x4d\x0b\x7a\x9e\xac"
$onenote_hdr = "\xe4\x52\x5c\x7b\x8c\xd8\xa7\x4d\xae\xb1\x53\x78\xd0\x29\x96\xd3"
$bat_contents01 = "@echo off" nocase
$bat_contents02 = "On Error Resume" nocase
condition:
$onenote_hdr at 0 and for any i in (0..#embedded_magic) : (
$bat_contents01 in (@embedded_magic[i]+36..@embedded_magic[i]+36+uint32(@embedded_magic[i]+16)) or
$bat_contents02 in (@embedded_magic[i]+36..@embedded_magic[i]+36+uint32(@embedded_magic[i]+16))
)
}
